Advancing Secure Communication in the Quantum Era through the Integration of Artificial Intelligence and Quantum Cryptographic Techniques
Author's Country: India
DOI:
https://doi.org/10.36805/fze4t734Keywords:
Quantum Computing, Quantum Cryptography, Quantum Key Distribution (QKD), Quantum Threat, Artificial Intelligence (AI), Secure CommunicationAbstract
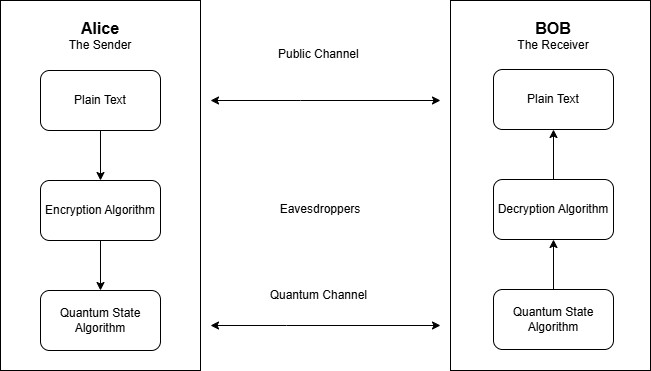
Utilizing the ideas of quantum physics, quantum cryptography is quickly becoming a vital defense against the growing cybersecurity risks of the contemporary day, especially in light of developing quantum computing. This essay investigates the complex field of quantum cryptography and looks at how it can transform network security and protect private data. We examine the fundamental ideas of quantum cryptography, such as Quantum Key Distribution (QKD) protocols like BB84 and E91, which use quantum features like superposition and entanglement to provide potentially indestructible secure communication channels. We also discuss the urgent need for quantum-resistant solutions in view of the developing "quantum threat" to well-known cryptographic algorithms like RSA and AES. The potential benefits and difficulties of using artificial intelligence (AI) techniques to boost quantum cryptography systems' resilience and efficiency are also examined. The creation of effective quantum repeater networks and enhanced security proofs are among the outstanding research topics, future difficulties, and present implementations in quantum cryptography that are covered in this study. We stress how crucial quantum cryptography is to protecting sensitive communications in the quantum era for a variety of industries, including the military, government, financial industry, and healthcare. We come to the conclusion that quantum cryptography has enormous potential for protecting vital information systems from future cyberattacks that are becoming more complex, even if we acknowledge the technology's early stages of development.
Downloads
References
[1] L. K. Grover, “A fast quantum mechanical algorithm for database search,” in Proceedings of the twentyeighth annual ACM symposium on Theory of computing, pp. 212–219, 1996.
[2] C. H. Bennett and G. Brassard, “Quantum cryptography: Public key distribution and coin tossing,” arXiv preprint arXiv:2003.06557, 2020.
[3] V. Scarani, H. Bechmann-Pasquinucci, N. J. Cerf, M. Dusˇek, N. Lu¨tkenhaus, and M. Peev, “The security of practical quantum key distribution,” Reviews of modern physics, vol. 81, no. 3, p. 1301, 2009.
[4] H.-K. Lo, H. F. Chau, and M. Ardehali, “Efficient quantum key distribution scheme and a proof of its unconditional security,” Journal of Cryptology, vol. 18, pp. 133–165, 2005.
[5] A. K. Ekert, “Quantum cryptography based on bell’s theorem,” Physical review letters, vol. 67, no. 6, p. 661, 1991.
[6] C. Weedbrook, S. Pirandola, R. Garc´ıa-Patro´n, N. J. Cerf, T. C. Ralph, J. H. Shapiro, and S. Lloyd, “Gaussian quantum information,” Reviews of Modern Physics, vol. 84, no. 2, p. 621, 2012.
[7] S. Pirandola, C. Ottaviani, G. Spedalieri, C. Weed- brook, S. L. Braunstein, S. Lloyd, T. Gehring, C. S. Ja- cobsen, and U. L. Andersen, “High-rate measurement- device-independent quantum cryptography,” Nature Photonics, vol. 9, no. 6, pp. 397–402, 2015.
[8] S. Wang, W. Chen, Z.-Q. Yin, H.-W. Li, D.-Y. He, Y.-H. Li, Z. Zhou, X.-T. Song, F.-Y. Li, D. Wang, et al., “Field and long-term demonstration of a wide area quantum key distribution network,” Optics express, vol. 22, no. 18, pp. 21739–21756, 2014.
[9] H.-K. Lo, M. Curty, and K. Tamaki, “Secure quantum key distribution,” Nature Photonics, vol. 8, no. 8, pp. 595–604, 2014.
[10] M. Lucamarini, Z. L. Yuan, J. F. Dynes, and A. J. Shields, “Overcoming the rate–distance limit of quantum key distribution without quantum repeaters,” Na- ture, vol. 557, no. 7705, pp. 400–403, 2018.
[11] Y. Zhao, C.-H. F. Fung, B. Qi, C. Chen, and H.-K. Lo, “Quantum hacking: Experimental demonstration of time-shift attack against practical quantum-key- distribution systems,” Physical Review A, vol. 78, no. 4, p. 042333, 2008.
[12] W.-Y. Hwang, “Quantum key distribution with high loss: toward global secure communication,” Physical review letters, vol. 91, no. 5, p. 057901, 2003.
[13] D. Elser, K. Gunthner, I. Khan, B. Stiller, C. Mar- quardt, G. Leuchs, K. Saucke, D. Trondle, F. Heine, S. Seel, et al., “Satellite quantum communication via the alphasat laser communication terminal-quantum signals from 36 thousand kilometers above earth,” in 2015 IEEE international conference on space optical systems and applications (ICSOS), pp. 1–4, IEEE, 2015.
[14] I. Derkach, V. C. Usenko, and R. Filip, “Continuous- variable quantum key distribution with a leakage from state preparation,” Physical Review A, vol. 96, no. 6, p. 062309, 2017.
[15] R. Kumar, H. Qin, and R. Alle´aume, “Coexistence of continuous variable qkd with intense dwdm classical channels,” New Journal of Physics, vol. 17, no. 4, p. 043027, 2015.
[16] D. J. Bernstein, T. Lange, and P. Schwabe, “The security impact of a new cryptographic library,” in Progress in Cryptology–LATINCRYPT 2012: 2nd International Conference on Cryptology and Information Security in Latin America, Santiago, Chile, October 7-10, 2012. Proceedings 2, pp. 159–176, Springer, 2012.
[17] M. Mosca, “Cybersecurity in an era with quantum computers: will we be ready?,” IEEE Security & Privacy, vol. 16, no. 5, pp. 38–41, 2018.
[18] D. Jao and L. De Feo, “Towards quantum-resistant cryptosystems from supersingular elliptic curve isogenies,” in Post-Quantum Cryptography: 4th Inter- national Workshop, PQCrypto 2011, Taipei, Taiwan, November 29–December 2, 2011. Proceedings 4, pp. 19–34, Springer, 2011.
[19] N. Sangouard, C. Simon, H. De Riedmatten, and N. Gisin, “Quantum repeaters based on atomic ensem- bles and linear optics,” Reviews of Modern Physics, vol. 83, no. 1, p. 33, 2011.
[20] M. Sasaki, M. Fujiwara, H. Ishizuka, W. Klaus, K. Wakui, M. Takeoka, S. Miki, T. Yamashita,
Z. Wang, A. Tanaka, et al., “Field test of quantum key distribution in the Tokyo qkd network,” Optics express, vol. 19, no. 11, pp. 10387–10409, 2011.
[21] A. I. Nurhadi and N. R. Syambas, “Quantum key distribution (qkd) protocols: A survey,” in 2018 4th International Conference on Wireless and Telematics (ICWT), pp. 1–5, IEEE, 2018.
[22] M. Kalra and R. C. Poonia, “Design a new protocol and compare with bb84 protocol for quantum key distribution,” in Soft Computing for Problem Solving: SocProS 2017, Volume 2, pp. 969–978, Springer, 2019.
[23] T. Sasaki, Y. Yamamoto, and M. Koashi, “Practical quantum key distribution protocol without monitoring signal disturbance,” Nature, vol. 509, no. 7501, pp. 475–478, 2014.
[24] B. Dirks, I. Ferrario, A. Le Pera, D. V. Finocchiaro, M. Desmons, D. de Lange, H. de Man, A. J. Meskers, J. Morits, N. M. Neumann, et al., “Geoqkd: quantum key distribution from a geostationary satellite,” in International Conference on Space Optics—ICSO 2020, vol. 11852, pp. 222–236, SPIE, 2021.
[25] J. Williams, M. Suchara, T. Zhong, H. Qiao, R. Ket- timuthu, and R. Fukumori, “Implementation of quantum key distribution and quantum clock synchroniza- tion via time bin encoding,” in Quantum Computing, Communication, and Simulation, vol. 11699, pp. 16– 25, SPIE, 2021.
[26] C. Schimpf, S. Manna, S. F. Covre da Silva, M. Aigner, and A. Rastelli, “Entanglement-based quantum key distribution with a blinking-free quantum dot operated at a temperature up to 20 k,” Advanced Photonics, vol. 3, no. 6, pp. 065001–065001, 2021.
[27] O. Amer, W. O. Krawec, and B. Wang, “Efficient routing for quantum key distribution networks,” in 2020 IEEE International Conference on Quantum Computing and Engineering (QCE), pp. 137–147, IEEE, 2020.
[28] H.-J. Ding, J.-Y. Liu, C.-M. Zhang, and Q. Wang, “Predicting optimal parameters with random forest for quantum key distribution,” Quantum Information Processing, vol. 19, pp. 1–8, 2020.
[29] A.-M. Dhoha, A.-K. Mashael, A.-A. Ghadeer, A.- A. Manal, M. Al Fosail, and N. Nagy, “Quantum cryptography on ibm qx,” in 2019 2nd International Conference on Computer Applications & Information Security (ICCAIS), pp. 1–6, IEEE, 2019.
[30] K. Yao, W. O. Krawec, and J. Zhu, “Quantum sam- pling for finite key rates in high dimensional quantum cryptography,” IEEE Transactions on Information Theory, vol. 68, no. 5, pp. 3144–3163, 2022.
[31] C. Mujdei, L. Wouters, A. Karmakar, A. Beckers, J. M. B. Mera, and I. Verbauwhede, “Side-channel analysis of lattice-based post-quantum cryptography: Exploiting polynomial multiplication,” ACM Transac- tions on Embedded Computing Systems, 2022.
[32] J. L. Iman˜a, P. He, T. Bao, Y. Tu, and J. Xie, “Efficient hardware arithmetic for inverted binary ring-lwe based post-quantum cryptography,” IEEE Transactions on Circuits and Systems I: Regular Papers, vol. 69, no. 8, pp. 3297–3307, 2022.
[33] A. Prakasan, K. Jain, and P. Krishnan, “Authenticated- encryption in the quantum key distribution classical channel using post-quantum cryptography,” in 2022 6th International Conference on Intelligent Computing and Control Systems (ICICCS), pp. 804–811, IEEE, 2022.
[34] P. Sajimon, K. Jain, and P. Krishnan, “Analysis of post-quantum cryptography for internet of things,” in 2022 6th International Conference on Intelligent Computing and Control Systems (ICICCS), pp. 387– 394, IEEE, 2022.
[35] S. Abidin, A. Swami, E. Ramirez-As´ıs, J. Alvarado- Tolentino, R. K. Maurya, and N. Hussain, “Quantum cryptography technique: A way to improve security challenges in mobile cloud computing (mcc),” Mate- rials Today: Proceedings, vol. 51, pp. 508–514, 2022.
[36] A. Kumar, C. Ottaviani, S. S. Gill, and R. Buyya, “Securing the future internet of things with post- quantum cryptography,” Security and Privacy, vol. 5, no. 2, p. e200, 2022.
[37] J. Ahn, H.-Y. Kwon, B. Ahn, K. Park, T. Kim, M.- K. Lee, J. Kim, and J. Chung, “Toward quantum secured distributed energy resources: Adoption of post-quantum cryptography (pqc) and quantum key distribution (qkd),” Energies, vol. 15, no. 3, p. 714, 2022.
[38] S. Gupta, A. Gupta, I. Y. Pandya, A. Bhatt, and K. Mehta, “End to end secure e-voting using blockchain & quantum key distribution,” Materials Today: Proceedings, 2021.
[39] Y.-Q. Lin, M. Wang, X.-Q. Yang, and H.-W. Liu, “Counterfactual quantum key distribution with un- trusted detectors,” Heliyon, vol. 9, no. 2, 2023.
[40] Y. Cao, Y. Zhao, J. Wang, X. Yu, Z. Ma, and J. Zhang, “Kaas: Key as a service over quantum key distribution integrated optical networks,” IEEE Communications Magazine, vol. 57, no. 5, pp. 152–159, 2019.
[41] H.-Y. Su, “Simple analysis of security of the bb84 quantum key distribution protocol,” Quantum Infor- mation Processing, vol. 19, no. 6, p. 169, 2020.
[42] Advisera, “What is the meaning of ISO 27001?” [Online]. Available: https://advisera.com/27001academy/what-is-iso-27001/.
[43] A. Agrawal et al., “Software security estimation using the hybrid fuzzy ANP-TOPSIS approach: design tactics perspective,” Symmetry, vol. 12, no. 4, p. 598, 2020, doi: 10.3390/SYM12040598.
[44] A. Aldoseri, K. N. Al-Khalifa, and A. M. Hamouda, “Re-thinking data strategy and integration for artificial intelligence: concepts, opportunities, and challenges,” Appl. Sci., vol. 13, no. 12, p. 7082, 2023, doi: 10.3390/APP13127082.
[45] H. Alyami et al., “The evaluation of software security through quantum computing techniques: a durability perspective,” Appl. Sci., vol. 11, no. 24, p. 11784, 2021, doi: 10.3390/APP112411784.
[46] U. Awan, L. Hannola, A. Tandon, R. K. Goyal, and A. Dhir, “Quantum computing challenges in the software industry. A fuzzy AHP-based approach,” Inf. Softw. Technol., vol. 147, p. 106896, 2022, doi: 10.1016/J.INFSOF.2022.106896.
[47] O. Ayoade, P. Rivas, and J. Orduz, “Artificial intelligence computing at the quantum level,” Data, vol. 7, no. 3, p. 28, 2022, doi: 10.3390/DATA7030028.
[48] C. H. Bennett and G. Brassard, “Quantum cryptography: public key distribution and coin tossing,” Theor. Comput. Sci., vol. 560, no. P1, pp. 7–11, 2020, doi: 10.1016/j.tcs.2014.05.025.
[49] M. Braverman, Y. K. Ko, and O. Weinstein, “Approximating the best Nash equilibrium in no (1ogn)-time breaks the exponential time hypothesis,” Proc. West Mark Ed Assoc Conf., vol. 2015, no. January, pp. 970–982, 2015, doi: 10.1137/1.9781611973730.66.
[50] A. Broadbent and C. Schaffner, “Quantum cryptography beyond quantum key distribution,” Des. Codes Cryptogr., vol. 78, no. 1, pp. 351–382, 2015, doi: 10.1007/S10623-015-0157-4.
[51] J. E. Catril Opazo, “NIST cybersecurity framework in South America: Argentina, Brazil, Chile, Colombia, and Uruguay,” 2021.
[52] E. Diamanti, H. K. Lo, B. Qi, and Z. Yuan, “Practical challenges in quantum key distribution,” NPJ Quantum Inf., vol. 2, no. 1, pp. 1–12, 2016, doi: 10.1038/npjqi.2016.25.
[53] W. Diffie and M. E. Hellman, “New directions in cryptography,” IEEE Trans. Inf. Theory, vol. 22, no. 6, pp. 644–654, 1976, doi: 10.1109/TIT.1976.1055638.
[54] K. M. Eisenhardt, “Building theories from case study research,” Acad. Manag. Rev., vol. 14, no. 4, p. 532, 1989, doi: 10.2307/258557.
[55] A. Elaziz and F. Raheman, “The future of cybersecurity in the age of quantum computers,” Fut. Internet, vol. 14, no. 11, p. 335, 2022, doi: 10.3390/FI14110335.
[56] H. Feistel, “Block cipher cryptographic system,” 1971.
[57] GDPR, “What is GDPR, the EU’s new data protection law?” [Online]. Available: https://gdpr.eu/what-is-gdpr/.
[58] S. S. Gill et al., “AI for next-generation computing: Emerging trends and future directions,” Internet of Things, vol. 19, p. 100514, 2022, doi: 10.1016/J.IOT.2022.100514.
[59] S. Gupta, S. Modgil, P. C. Bhatt, C. J. Chiappetta Jabbour, and S. Kamble, “Quantum computing-led innovation for achieving a more sustainable Covid-19 healthcare industry,” Technovation, vol. 120, p. 102544, 2023, doi: 10.1016/J.TECHNOVATION.2022.102544.
[60] L. Gyongyosi and S. Imre, “Secret key rate adaption for multicarrier continuous-variable quantum key distribution,” SN Comput. Sci., vol. 1, no. 1, pp. 1–17, 2020, doi: 10.1007/s42979-019-0027-7.
[61] ICO, “Information Commissioner’s Office (ICO): The UK GDPR, UK GDPR guidance and resources,” [Online]. Available: https://ico.org.uk/for-organisations/uk-gdpr-guidance-and-resources/.
[62] ISO, “ISO/IEC 27035–1:2016—Information technology—Security techniques—Information security incident management—Part 1: Principles of incident management,” [Online]. Available: https://www.iso.org/standard/60803.html.
[63] ISO, “ISO/IEC 27001 and related standards Information security management,” 2022.
[64] C. Johnson, L. Badger, D. Waltermire, J. Snyder, and C. Skorupka, “Guide to cyber threat information sharing,” NIST Spec. Publ., 2016, doi: 10.6028/NIST.SP.800-150.
[65] M. Kumar, “Post-quantum cryptography algorithm’s standardization and performance analysis,” Array, vol. 15, p. 100242, 2022, doi: 10.1016/J.ARRAY.2022.100242.
[66] V. Lovic, “Quantum key distribution: advantages, challenges and policy,” 2020, doi: 10.17863/CAM.58622.
[67] G. M. Mallow et al., “Quantum computing: the future of big data and artificial intelligence in spine,” Spine Surg. Relat. Res., vol. 6, no. 2, p. 93, 2022, doi: 10.22603/SSRR.2021-0251.
[68] NIST, “Advanced Encryption Standard (AES),” 2001. [Online]. Available: https://web.archive.org/web/20170312045558/http://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.197.pdf.
[69] A.-M. Udroiu, M. Dumitrache, and I. Sandu, “Improving the cybersecurity of medical systems by applying the NIST framework,” in Proc. 14th Int. Conf. Electron. Comput. Artif. Intell. (ECAI), IEEE, 2022, pp. 1–7.
[70] M. Ying, “Quantum computation, quantum theory, and AI,” Artif. Intell., vol. 174, no. 2, pp. 162–176, 2010, doi: 10.1016/J.ARTINT.2009.11.009.
[71] Radanliev, P. Artificial intelligence and quantum cryptography. J Anal Sci Technol 15, 4 (2024). https://doi.org/10.1186/s40543-024-00416-6
[72] M. S. Akter, J. Rodriguez-Cardenas, H. Shahriar, A. Cuzzocrea and F. Wu, "Quantum Cryptography for Enhanced Network Security: A Comprehensive Survey of Research, Developments, and Future Directions," 2023 IEEE International Conference on Big Data (BigData), Sorrento, Italy, 2023, pp. 5408-5417, doi: 10.1109/BigData59044.2023.10386889.
Downloads
Published
Issue
Section
License

This work is licensed under a Lisensi Creative Commons Atribusi-BerbagiSerupa 4.0 Internasional.



